

So long, passwords! What exactly are passkeys?
The FIDO Alliance has developed passkey technology with Google. The aim is to eliminate passwords and make logins more convenient but still more secure. But how exactly does it work?
The topic of passkeys is on everyone’s lips right now. This technology was developed by the FIDO Alliance, which includes many big players in the tech industry, including Google, Microsoft, Apple and Amazon. FIDO is an abbreviation of Fast Identity Online – i.e. fast online identification. The idea behind passkeys is that you have access to all of your online accounts without having to log in with a username and password every time, not to mention cumbersome two-factor authentication (2FA).
Instead, you can authenticate yourself on your phone or laptop – including using facial or fingerprint recognition. You’ll then be logged in automatically. Theoretically, you no longer need passwords at all. It’s faster and more convenient than passwords and 2FA. Plus, it’s safer. But how?
What are passkeys and how do they work?
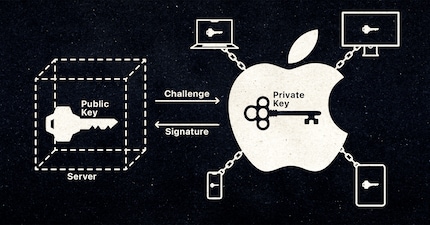
The clue’s in the name. Passkeys are keys to get in or past somewhere. More precisely, they’re a pair of keys. One half consists of a public key that’s saved for storage on the web server of the website or service. The other half consists of the private, asymmetric crypto key. Simply put, you can think of it as a very long, completely randomly generated sequence of characters. This private key is then stored on a device of your choice, such as your smartphone or laptop. Nobody ever finds out exactly how it’s made up. Not even if you use it to log in somewhere.
Because, unlike the password query, it’s not you who sends your password to where you want to log in. It’s the exact opposite: it’s the online service – for example your Google account – that sends a request to the device where your private key is stored. The authenticator on your device has to solve this «challenge».
Once the authenticator has done this, it sends the solved challenge back to the online service. It now decides using the public key that: «The task was solved correctly, so the recipient had the correct key. Access granted.» In doing so, you have essentially proven that you are who you say you are and that you have the key, without revealing exactly what your private key is made up of.
You can determine exactly what the authenticator on your device is. It could be a master password, a PIN, a pattern on your smartphone’s touchpad, or simply your fingerprint or facial recognition. This depends on what’s supported by the device where the key is stored.
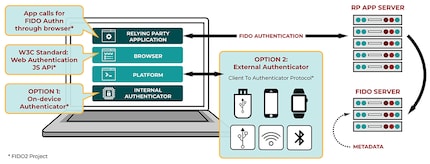
The basis for passkeys: FIDO2
Passkeys are an extension of FIDO2. Maybe you’ve already heard of it. FIDO2 was also developed by the FIDO Alliance and the World Wide Web Consortium (W3C). It consists of two «ingredients»:
- Client to Authenticator Protocol (CTAP2).
- WebAuthentication standard API (WebAuthn).
Put simply, CTAP2 ensures that the hardware authenticator – e.g. a security token such as Yubikey – and the browser can communicate securely with each other. CTAP2 supports USB, Bluetooth and NFC. This restricts the private key to one device. I’ll get to that in a moment.
WebAuthn, meanwhile, is an interface responsible for communication between an authenticator and the online service you want to log into. If an online service supports Webauthn, you can log in using the key principle explained above.
Source: FIDO Alliance
The FIDO Alliance originally wanted to retire the classic password with FIDO2. However, they had the problem that the private key with FIDO2 was tied to one specific device. The principle wasn’t very convenient for users. If you have several devices that you want to use as an authenticator – for example a personal and a business smartphone – you have to link each of the devices separately to each individual service. Each device gets its own private key. If you’ve only linked a device that you don’t have with you, there’s no way to log in. The conventional password system was more convenient. That’s why the FIDO Alliance refined the standard for passkeys. Nothing changed in principle. The only difference is that with passkeys, the private key can be synchronised between multiple devices.

A practical example: Apple
Apple, for example, has implemented passkeys in its Keychain (since macOS Ventura and iOS/iPadOS 16). If you have activated login via passkey for a service, such as your Google account, logging in works on your Mac, your iPhone or your iPad – provided you use the same Apple ID for all Apple devices. So, as soon as you’ve started up your Mac with the password, the private key is active.
Source: Florian Bodoky.
On iPhones, the authenticator can also be facial recognition. Once you’ve completed this when unlocking your iPhone, you can log in to Google in your smartphone’s browser without a password. Smartphones – regardless of whether they’re Android (from Android 9) or iOS – also offer an additional function.

Source: Florian Bodoky
You can use them as an authenticator device to log in to another device. For example, if you’re at a friend’s house and want to log in to your Google account on their PC, you can do this using the authenticator on your phone (because that’s where the private key is stored).
Source: Kolide
The manufacturers clearly explain step by step how to activate passkeys for services or devices. I’ll link you to the instructions from Apple, Google and Microsoft here. But a quick Google search will bring up instructions for other providers.
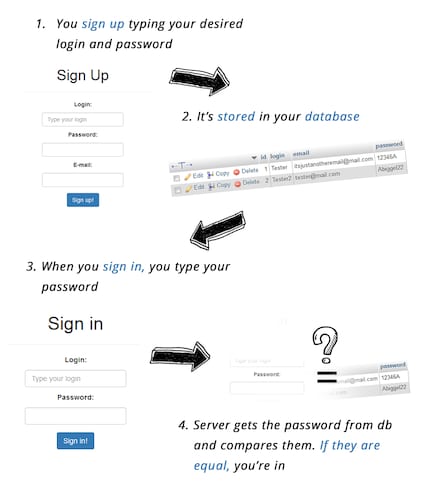
How do they differ from passwords?
Passkeys and passwords have a completely different approach. While passkeys work as described above, passwords are stored in the respective services’ databases, albeit encrypted. If you enter the password together with the username, the online service compares this information. If they’re identical, you’ll be granted access.
Source: DigiCert
The weaknesses of this system are obvious. There’s no need for proof that «you» are actually you. Anyone who knows your password and username can gain access to your account. This can happen very quickly – your passwords can fall into the wrong hands through phishing, scam calls or even a hack on the online service. Cyber criminals leave no stone unturned. Fake e-mails in bad English are a thing of the past – phishing e-mails are getting better and better and even redirect you to precisely replicated websites of government institutions or companies. According to Microsoft, there are 579 password attacks per second worldwide, which is 18 billion per year.
Source: NCSC
The fact that your data ends up on the internet without you doing anything isn’t as rare as you think. Last year, Trend Micro (website in German) published a study on cyber attacks on companies. According to this, 88 per cent of all companies surveyed fell victim to cyber attacks that resulted in the loss or theft of customer data.
As your private key is never transmitted with passkeys, it can’t be intercepted or stolen from the online service.
Passwords are also much more difficult to manage: you should use different passwords for all services, otherwise cybercriminals can hack several of your accounts at once if they only steal one password. Passwords shouldn’t be too simple – a brute force attack is enough to crack passwords like «Test1234». So that you can remember these many passwords, you need a password manager.
Or you can activate the two-factor authentication process, where you confirm that you are really you using an authentication app or SMS code. This is quite complicated and sometimes error-prone. For example, if you enter the 2FA code incorrectly, you have to repeat the process. Passkeys don’t just solve the problem of a lack of security. They also simplify and speed up the registration process for online services.
Which services support passkeys?
The best-known companies that support passkey technology are Google, Microsoft and Apple. But there are many others. A few more will probably be added as I write this article. I recommend Passkeys.directory. It’s is a public registry containing services that already support passkeys. You can also vote for your favourite service there if it doesn’t yet support passkeys. That then tells them that there are people who want them to integrate passkeys. Who knows? Maybe that’ll include Digitec and Galaxus.
Header image: Shutterstock
I've been tinkering with digital networks ever since I found out how to activate both telephone channels on the ISDN card for greater bandwidth. As for the analogue variety, I've been doing that since I learned to talk. Though Winterthur is my adoptive home city, my heart still bleeds red and blue.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all


