
Background information
An introduction to hacking – how to launch Command Prompt with MSPaint
by Dominik Bärlocher
Is a PDF really a PDF? Yes, says your computer. No, we say. Because we can use simple means to trick a user into believing that they are looking at file type A, but are actually looking at file type B.
Hackers don't just rely on themselves. It is often a user in the target system that opens the door to criminals. After all, why would a hacker break through a firewall if they can bypass it? Better still, why would a hacker bother if a user can simply be made to believe that they are only opening a harmless image?
Let's recreate an attack that targets the victim's cluelessness.
Before we start with the script, we need to make a setting in Windows, if you have not already done so. In the second step, we need file name extensions. These are the letters after the dot in each file name. A picture from the internet is usually a .jpg, a Word document is a .docx, a video is a .mp4 and so on. However, as Microsoft thought at some point that this would only confuse inexperienced users unnecessarily, they have hidden the file name extensions by default.
But we need them, certainly only in one folder.
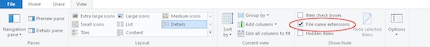
Voilà, that's it for now. Let's go programming
Every attack by a hacker of this type consists of two parts.
In this article, I will explain how you can recreate a very simple attack. Your computer will display a JPG, but in reality we have a small programme that simply opens digitec.ch. For the sake of simplicity, we will use a batch script, i.e. a bat file. Not because hackers particularly like using them, but simply because any Windows computer can easily handle them.
start "" https://digitec.ch
3. Save the file as digitec_jpg.bat in your hack_the_planet folder
The code does nothing other than open your default browser and call up the digitecs website. So nothing crazy. If you come across bat files in the wild or in your email inbox, be careful, because opening a URL is far from all they can do.
In the context of this one bat file, however, we can trust the file because we programmed it ourselves.
The technique we use today is called Right-to-Left Override, RTL Override, or RTLO. Essentially, we instruct the computer to change the reading direction in the middle of the file name. To do this, we need a special character that changes the direction of the text. This is the RTLO. The RTLO exists because there are languages such as Arabic or Hebrew. These are written and read from right to left, not from left to right like our alphabet.
The easiest way to do this is with a feature that comes with Windows: The character map. This is a list of all the characters that you can write with your computer.
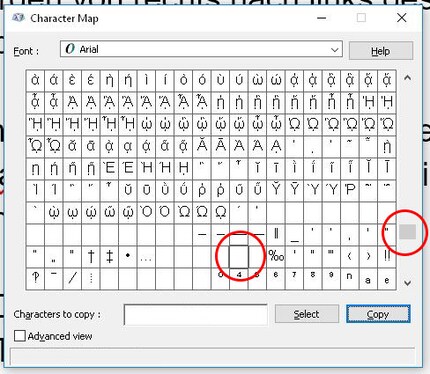
At the beginning it is quite simple. In the end, our file - currently called digitec_jpg.bat - should be called digitec_tab.jpg. So you can already see where we are going to rotate the text. The format of a file name with RTLO goes like this: $filename + RTLO + $realFileExtensionRueckwarts + $falseFileExtension
In our case, it looks like this:
So we compose the file name as follows
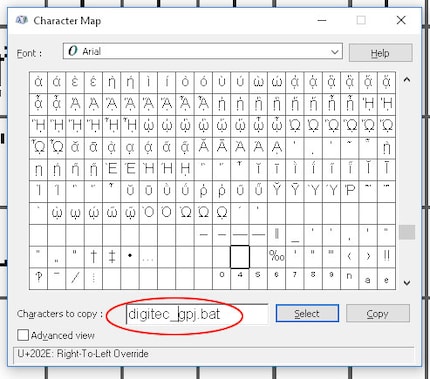
The file name currently still looks a bit strange and incorrect. This is because the RTLO is there but is not displayed correctly. I can't tell you why this is the case.
Currently, the new file name that we put together in the character map is in the clipboard. Therefore: Back to the hack_the_planet folder. The digitec_jpg.bat file is ready there.
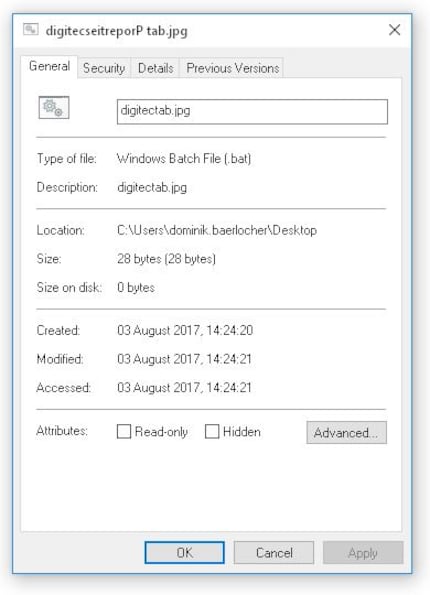
Voilà, the file now looks as if it is called digitec_tab.jpg. When you open it, you activate the above script and digitec opens. In short, hackers can make you believe that you are opening an image, but in reality you are executing malicious code.
"Yes, but", I hear you say, "everyone can see straight away that it's not a jpg. The file name has only been minimally obscured!"
True. In our case, it's all obvious, but that's also the point of the exercise. So you can see what happened from A to Z. But imagine the file has a random name like "iYYprTjZEETAb.jpg". Such and similar naming schemes are used by social networks and content delivery networks (CDN), which often leads to such file names not being questioned.
This is of course not only possible with .bat, but also with a variety of other file formats. The most effective are probably:
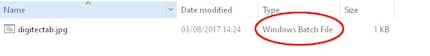
Protection against this attack is very simple. Instead of just opening everything that is put in front of you: Be suspicious. You can also detect this type of attack quite quickly by switching the view to "Large icons" in the view options of your folder. This is because the icon of the true file type is displayed where a small preview would otherwise appear.
Or even better, but much less pretty: Set the view to "Details", because your computer recognises the file for what it is. This attack really only deceives the user, not the machine.
Furthermore, you're in luck: Many anti-malware programmes automatically filter these files, warn you and the system sometimes refuses to execute the code. In the case of our .bat, however, you will notice that no checks have been made. Hence this article.
Nevertheless: If you are looking for the most cumbersome way ever to create a shortcut, you can now do so with a .bat disguised as a .jpg.
Above, in the main image of this page, I asked if you could see the camouflaged snake. Here it is:

Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all