
After the hacker attack: How you can protect yourself from brute force attacks
Switzerland has been hit by a brute force attack. The federal government has responded and put a tool online that you can use to find out whether your account has been affected. As the attack is targeting passwords, let's take a look at passwords and strategies.
The Reporting and Analysis Centre for Information Assurance Melani warns: A large-scale attack has been registered in Switzerland. The attackers have unleashed a brute force attack on a server in Switzerland and compromised 21,000 usernames and passwords.
I'd like to take this as an opportunity to explain the concept of a brute force attack and give you some advice at the end on how you can help to ensure that such attacks remain largely ineffective.
What is a brute force attack?
Brute force attacks are attacks that essentially - and in somewhat simplified terms - do the following:
- Calls up the login form of the site
- Enters an email address as login
- Tries out password after password, following a dictionary
- The server responds with either "Password incorrect" or "Login successful"
- If "Password incorrect" is sent in response, the attacker tries the next word in the dictionary
The dictionary used in such an attack does not necessarily have to resemble a dictionary, because hackers know about passwords such as "eCSD,827c" and naturally try to break accounts with such monsters. The attack therefore starts with "a" and works its way through "aa" to "99999999". Attention, we are still simplifying here. In Regular Expression - an incredibly practical, machine-readable abstraction of character strings - a dictionary can look something like this:
Update: User YouShook figured out what was bugging me. I have adjusted the regex. Thank you, YouShook.
[a-zA-Z0-9\w]{6,8}Should fit. If not, please leave me a comment with the correct regex. The longer I stare at it, the less [\w] seems to be correct.
Translated, the regex means the following:
- [\w]: All punctuation marks
- {6,8}: Between six and eight characters long, as it makes no sense to test shorter passwords
The RegEx not only tests strings of special characters, but also words. So if your password is "digitec1", then this is included in the RegEx, because the RegEx does not differentiate between human words and random character strings.
In most cases, a brute force bot proceeds according to a list of email addresses or other login names purchased online and tries its dictionary per account.
- hans.muster@example.org/aaaaaa
- hans.muster@example.org/aaaaaaa
- hans.muster@example.org/aaaaaaaa
- ...
Depending on the bot's computing power and latency in the target, such an attack can be over in minutes or last several hours.
However, there are variants of a brute force attack. The one described above is the simplest, but also the most complex. However, hackers are lazy and often take advantage of statistics. Wikipedia maintains a list of the most commonly used passwords, which has been compiled after analysing hacks with significant data leaks.
A third variant is that the hackers buy a list of usernames and passwords from another hack and then apply these username/password combinations, i.e. the credentials, to a site. This attack can be very effective as many users have the nasty habit of using the same password and login for multiple sites and also as access to their credit card. It is therefore possible that the credentials from site A also work on site B.
After reading the Melani report, I suspect that the third variant was used in the attack. It's not explicitly stated, but reading between the lines it strongly feels that way. In particular, their check tool also indicates that the Melani is in possession of the list used by the attackers.
What can I do?
Melani responded promptly and launched a checktool online, which can be used to check the email addresses and login names of affected accounts. However, as the check tool is currently very popular with users, the server may be brought to its knees. Probably the most comprehensive alternative to the federal government's check tool is HaveIBeenPwned by security researcher Troy Hunt.
Yes, but my password is already "eCSD,827c" and that's not secure?
Passwords are a tiresome topic that will probably not be discussed any time soon. You and I know password guidelines like the following.
- At least eight characters long
- At least one number, with 1 being discouraged
- At least one special character
In RegEx, by the way, it looks like this
[a-zA-Z0-9\w]{8,}At the end you have something like eCSD,827c as a secure password. Or something like "d!gItec1". Both work, but are more practical for machines and less for humans. Because it is difficult to memorise something like this. The thought "It's digitec1, but the first i is a ! and the second is capitalised" is not very intuitive. I would therefore like to suggest an alternative solution that works quite well in itself.
It is the so-called xkcd password, named after an issue of the webcomic xkcd.
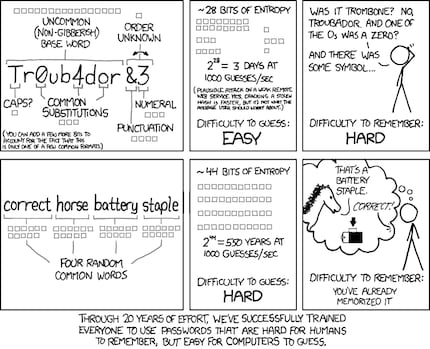
The theory behind the password is simple:
- Take three or four human-readable words and string them together
- Take a number as a separator or a special character
- Add something to the end, either a separator or a number
At the end you will have a password like "cat_confused_london5". Long enough, you've already memorised it and the only abstract thing about it is the number at the end. And a 5 is easy to remember. The password is 23 characters long, so an attack that starts with eight characters will sooner or later get past the confusing cat, but it will take a very, very long time.
This still doesn't solve the problem with "multiple sites, one password".
"But I don't want to have to remember a hundred passwords!"
It's understandable that having to remember several passwords is tedious. There are password managers such as KeePass for this purpose - security researcher Veit Hailperin has familiarised himself with the programme in detail - or, for those who prefer it as a browser plugin, LastPass.
LastPass faced a security leak a few months ago, discovered by Google researcher Tavis Ormandy, but now seems to have the problem under control. The premium version of LastPass costs 22.75 francs per year. The price is also controversial, as LastPass cost 11.37 francs until recently.
With both managers, it is possible to assign and save passwords without ever seeing the password. I find that kind of creepy, but it works well.
If you still want to use the same password everywhere, Melani recommends the following measures:
- Change the password of all online accounts that are linked to the affected email address (email account, online shops, e-banking, social media, etc.).
Use a separate password for each internet service/online portal.
- Enable 2-factor authentication wherever possible.
- Check any kind of bank statements, iTunes debits, etc. over the next few weeks. If you notice any irregularities, please contact your bank or the relevant company immediately.
- Inform all persons listed in the e-mail contacts that they should be careful when receiving e-mails with your sender and, if in doubt, contact you.
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all