
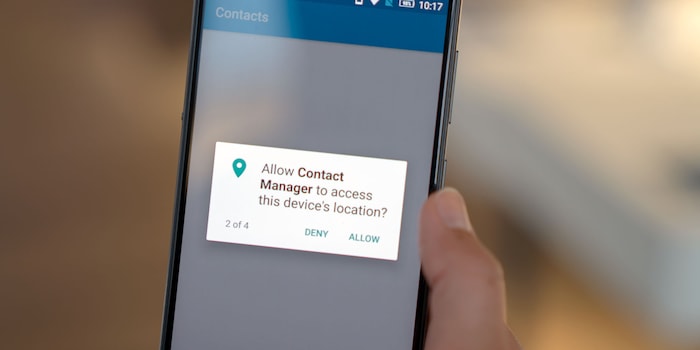
Permissions: What your phone wants from you
Every app on every phone asks you for permission to access components and software. It is difficult to handle permissions sensibly, as they are usually opaque. What's more, you often simply accept them without questioning. A look at what is probably the most broken feature in the smartphone world.
"You, I don't want this mobile," says a customer in the Zurich shop.
She has just received a replacement mobile phone from digitec's fleet of replacement phones and is setting up the Lenovo P2 in the shop. The phone is the model that the shop assistants give you when they have to send yours in. The P2 was chosen because it is inexpensive, powerful and stable, so it should survive several customers. It has replaced the Wiko Highway Star, which has served well for years.

So why doesn't the customer want it?
"The contact app on my mobile wants access to my location. I don't want that."
Good thinking. A contact app really shouldn't have to access location data. And why should it? The app reads your Google contacts and displays them in Lenovo's design. That's all it should do. Perhaps it needs the "Camera" permission if the app allows you to take a photo of your colleague and then use it as a contact picture. But "Location" is a bit absurd.
The workaround for the customer is simple: Google Contacts also needs a mountain of permissions, but not the location data. This mountain may sound threatening, but it is not. Let's take a look at this in detail.
The permissions mountain taken apart
Understanding permissions requires some understanding of your phone's hardware. Your phone is not a box of black magic, it's a computer. Computers always follow logic, even if you have to think outside the box to understand them.
So here's a quick interlude in which I'm going to de-blacken the black magic for you.
Interlude: Why a torch app needs access to your camera
A good example of how you need to think outside the box is the torch app. If you're looking for something in the dark, the torch on your phone is a lifesaver. After all, who always has a torch to hand? Most new phones have a torch built into the Android ROM. However, if this is not the case, you can use a flashlight app.
As soon as you install the app, the app asks for the "Camera" permission. Why?
The torch on your phone is actually not a torch at all. It is the camera's flash, which is not actually a flash, but simply an LED light bulb. Furthermore, this LED is part of your phone's camera system.
When you switch on the torch, you are essentially telling the phone "You're going to flash until I tell you to stop." To do this, the app has to talk to the camera system. Hence the "Camera" permission. There is also the "Control Flashlight" permission, for obvious reasons.
Google Contacts at permission level
So, now we have an example. Let's now take the permissions of Google Contacts apart. The app does require some permissions, but not without reason. I had to do a bit of guesswork when interpreting the permissions, as Google does not clearly communicate what the permissions are actually used for.
Identity
- find accounts on the device: Access to accounts that are linked to the phone, i.e. Google, Facebook, LinkedIn...
- add or remove accounts: Manage the accounts found above
- read your own contact card: Read your own contact details
- modify your own contact card: Customise your own contact details
Calendar
- read calendar events plus confidential information: enter birthdays, send appointment invitations, ....
Contacts
- find accounts on the device: access accounts that are linked to the phone, i.e. Google, Facebook, LinkedIn...
- read your contacts: Read out contact data
- modify your contacts: Change contact details on your account only. Changes here will not change the contact details of your friends. For example: You save your mum not under her name but as "Mummy"
SMS
- read your text messages (SMS or MMS): Association of contact with text messages
Phone
- directly call phone numbers: Call directly from the contact app, often the reverse of this function is stored in the phone app of the phone
- read call log: Call log, often contacts, ...
- read phone status and identity: Important if you have categorised your contacts and certain contacts may disturb you despite sleep mode
Photos / Media / Files
- read the contents of your USB storage: photos of your contacts, assign photos to contacts
- Storage: The app generally needs access to the storage for this
- read the contents of your USB storage: General access to the USB storage (if available)
- Device ID & call information: Important for calls. Can the phone ring? Which phone is ringing? Which image must be displayed
- read phone status and identity: Important if you have categorised your contacts and certain contacts are allowed to disturb you despite idle mode
Other
- read sync statistics: When was the last time the contacts were synchronised with the backup in the cloud?
- receive data from Internet: The app is allowed to synchronise the backup
- view configured accounts: The app is allowed to view the Google accounts on your phone
- view network connections: How strong is the network connection? Is WLAN on or off? This is relevant if we are considering Voice over LTE (VoLTE)
- full network access: In order for the app to synchronise backups and make phone calls, it needs access to the data network as well as the telephone network
- control Near Field Communication: contact exchange via NFC
- read sync settings: Can view the synchronisation settings on the phone
- run at startup: Starts up when you switch on the phone
- use accounts on the device: Can use the accounts on the phone, can switch directly from the contact app to WhatsApp if you select the option
- control vibration: Important if you have categorised your contacts and certain contacts are allowed to disturb you despite sleep mode
- prevent device from sleeping: The phone does not simply switch to standby when you are on a call
- modify system settings: May change synchronisation settings and other settings
- toggle sync on and off: May change synchronisation settings and other settings
- install shortcuts: Can create shortcuts to contacts on your home screen
- read Google service configuration: Can view the Google settings
The bigger problem with permissions
In newer versions of Android, your phone will ask you whether you want to grant or deny the app permission. If an app is well programmed, then the functionality of the app is by and large not affected by this. You can still view pictures on Instagram if you deny the app access to the camera.
Things get hairy when you have the same problem as the customer in the shop. She withdrew permission for the contact app on the P2 to access the location data. The app crashed immediately. When it restarted, the app asked for permission again. Denied again. Crash again. Restart again. Question again. The loop is endless. This is bad coding on the part of Lenovo on the P2. Since there are a large number of contact apps in the Play Store, Lenovo has apparently given up developing its own contact app. According to reports and the Lenovo Support Pages, Lenovo has been relying on Google Contacts since May 2018 at the latest.
The problem with "Yes, go on, OK"
As much effort as Google and other Android developers put into permissions, it's a labour of love. The reason for this is you. Unfortunately, most users don't scrutinise permissions. When they install an app, they simply click on "Yes", "Next", "Allow" and "OK".
While this is legitimate behaviour, it doesn't help the overall situation of questionable permissions. Sure, Lenovo is probably up to no good if they want the location data for a contact app. Could be a feature that shows you how far away a contact is from you
.
Other apps are after your data or simply use your user behaviour to generate traffic for advertising purposes. One example of this is the TouchPal app. The keyboard bombards you with adverts, even if you have purchased the "No Ads" Premium Pass. The comments in the review columns are full of "Showing adverts again".
So my advice: think about what permissions you give your apps. Be conservative and try out what happens if you don't give the permission. Better less than more. If you deny a permission that renders the app inoperable, simply restart the app and it will ask for the permission again.
What can happen if everything goes wrong
To conclude this article, I would like to quickly discuss the worst-case scenario: If you give an app too many permissions and someone does something bad with your phone.
The threat researchers at Trend Micro have put together a gallery of the twelve most abused permissions.
- Network-based location: attacks that have a precise location or a defined target area. For example: If you're in Russia, criminals can redirect you to Russian sites that mean you harm
- GPS Location: Used in the distribution of attacks and malware with a defined target area
- View Network State: Malicious apps seek out existing network connections so that other commands and routines are executed, including malware downloads and sending text messages. The apps can establish and terminate network connections without you doing anything, drain your battery and use up data volume
- View WiFi State: Criminals can use device bugs to steal WiFi passwords and hack into the networks you use
- Retrieve Running Apps: Criminals can steal information that flows through currently running apps. They can also switch off security apps
- Full Internet Access: Malicious apps can communicate online with their command centres or download malware
- Read Phone State and Identity: A favourite target of malware and information-stealing apps
- Automatically Start at Boot: This automatically launches a malicious app when you switch on your phone
- Control Vibrator: Used when an app needs some time to intercept information from emails, text messages and other messages
- Prevent from Sleeping: Malicious apps use this permission to keep your phone constantly active so that it executes malicious code. This can also drain your battery
- Modify/Delete SD Card Contents: Criminals store copies of stolen data on your SD card before passing it on to a command centre. Malware can also delete photos and other personal data on your memory card
- Send SMS Messages: Suppliers of premium services can use this permission to send paid SMS messages from your phone to a number they control. This increases your mobile phone bill and also allows them to communicate with command centres
Most of these permissions are misused to open the door for criminals to either abuse your smartphone for its computing power or to harvest information. Only one of them can cause you direct financial harm and only one of them can lead to data loss.
Nevertheless: It is advisable to only grant permissions where absolutely necessary.
Journalist. Author. Hacker. A storyteller searching for boundaries, secrets and taboos – putting the world to paper. Not because I can but because I can’t not.
Interesting facts about products, behind-the-scenes looks at manufacturers and deep-dives on interesting people.
Show all