
Guide
Synology NAS Upgrade – 2.5 Gigabits with a USB LAN adapter
by Martin Jud

Is your NAS sufficiently protected against a hacker attack? Mine was not. But now I have improved it.
This article will help you to avoid any major blunders when setting up a NAS. The security tips start with the first title. But first a foreword, which is honest but I don't like writing.
I apologise for the storm in a teacup. Due to sudden, persistent speed problems and my IP being published on the Internet by mistake, I was afraid that I had configured it badly and that someone was fiddling with my NAS.
I only found the error after hours of studying system logs and testing on a network that was isolated from the Internet. The problems were not caused by external influences, but by a defective LAN port on my Synology DS918+. My NAS has two LAN ports, which is why I notice the defect in the first place. Even though this is annoying, I'm very glad it didn't get worse.
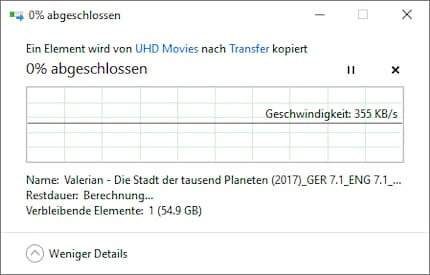
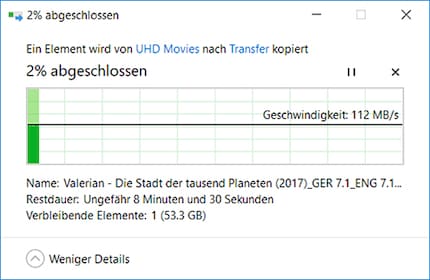
As you can see, my first LAN port only delivers around 350 kilobytes per second, but the second one works as it should.
So my NAS is up and running again. But what gives me pause for thought is that, as I feared, I made some major blunders when configuring it. I actually forgot to redirect two standard ports correctly. This meant that the login pages for the web interface and the Plex server were accessible to interested parties. Ouch - I should be pilloried for that!
If something like this happens to you, don't be surprised if some script kid steals your film database or misuses the CPU of the NAS for coin mining.
No system offers complete protection against misuse. But if you think about the basics before setting up a home network or NAS, you can protect yourself to a large extent. Take enough time to inform yourself and set up your NAS carefully. Don't get distracted in the process.
Be aware that network scans and attacks are carried out around the clock on the internet. Even if you configure and secure your network hardware well, you will never be able to rule out the possibility of someone accessing your data. Apart from that, a NAS does not serve as a backup medium. All the more reason not to store important files on the NAS. Only store what you can live with if it falls into someone else's hands.
Before you connect your NAS to the network, you should first take a look at your router. It is the first line of security in your network. You should check/implement the following points. Of course, these also apply to your NAS:
Consider carefully which services you want to use on your NAS. And in particular, which services you want to make accessible outside the local network. The fewer port forwardings you set up, the smaller the chance of being hacked at some point. For example, if you only use SFTP access to your NAS sporadically, it is recommended that you only forward the relevant ports for the times when you really need access. It is also advisable to only allow forwarding for IPs from the countries in which you are located.
Port forwarding pitfalls
If you set up your Internet access on a Synology NAS using the wizard or activate a new service, port forwarding is automatically suggested to you.
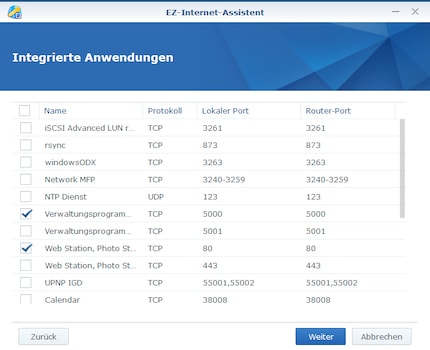
Unfortunately, the system does not inform you that it is not a good idea to use standardised ports. The manufacturer of the NAS should make improvements here. Because if you have activated Universal Plug and Play (UPnP) on your router or you operate your NAS in a demilitarised zone (DMZ), the suggested rule or the suggested security risk will be adopted.
How to forward ports correctly
The best thing to do is to deactivate UPnP on the router and create the port forwarding manually. You can find out how this works for your router either in the manual or on this page. Of course, if you have not already done so, you must first assign a fixed IP to your NAS. You can also find out how this works on the aforementioned homepage.
If you want to make sure you don't catch any default ports, we recommend taking a look at this list. Make sure not to open any of these ports. For example, if you want to enable TCP port 5001 for encrypted access to the Synology web interface, set a different port for the router port. For example, port 26953, which means that your open port will only be found if someone performs a scan in the corresponding area.
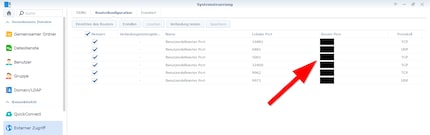
You can find the port forwarding rules in Synology under "Control Panel/External Access/Router Configuration". If you have configured the forwarding manually on the router side and also enter the rules here, you can test whether the ports are working from the NAS interface. Please do not forget to create/check the firewall rules of the NAS for the respective services. On Synology, you can find these under "Control Panel/Security/Firewall". As already mentioned, it is a good idea to enable services/ports in the firewall only for certain countries.
Test whether an unwanted port is open
Once you have finished port forwarding, you should test whether a loophole has been left open somewhere. To do this, perform a port scan. You can do this, for example, from this homepage.
Enter your IP and the standardised ports to be scanned and off you go. If you have done everything correctly, you will not receive any feedback from the ports:
Scanning ports on 178.xx.xxx.xx
178.xx.xxx.xx isn't responding on port 21 (ftp).
178.xx.xxx.xx isn't responding on port 23 (telnet).
178.xx.xxx.xx isn't responding on port 25 (smtp).
178.xx.xxx.xx isn't responding on port 80 (http).
178.xx.xxx.xx isn't responding on port 110 (pop3).
178.xx.xxx.xx isn't responding on port 139 (netbios-ssn).
178.xx.xxx.xx isn't responding on port 443 (https).
178.xx.xxx.xx isn't responding on port 445 (microsoft-ds).
178.xx.xxx.xx isn't responding on port 1433 (ms-sql-s).
178.xx.xxx.xx isn't responding on port 1521 (ncube-lm).
178.xx.xxx.xx isn't responding on port 1723 (pptp).
178.xx.xxx.xx isn't responding on port 3306 (mysql).
178.xx.xxx.xx isn't responding on port 3389 (ms-wbt-server).
178.xx.xxx.xx isn't responding on port 5900.
178.xx.xxx.xx isn't responding on port 8080 (webcache).
178.xx.xxx.xx isn't responding on port 5000 (commplex-main).
178.xx.xxx.xx isn't responding on port 5001 (commplex-link).
178.xx.xxx.xx isn't responding on port 32000.
Encrypted transmission should not only be used for all your NAS services. It should also be used on the network in general. This is because encryption guarantees the authenticity of transmitted data. Thanks to HTTPS, what the server sends to you arrives. This prevents manipulation or man-in-the-middle attacks.
Here is an example of how you can enable SSL for accessing the web interface of a Synology NAS:
It is recommended that you then create a certificate registration request and import a signed certificate. If you do not do this, your browser will complain that the certificate is not trustworthy when it is accessed. You can find more information on how this works with Synology here.
Consider using a VPN server. If you access your LAN via Virtual Private Network, this will give you a lot of security. If set up properly, even your internet service provider will not be able to see what you or your NAS are doing on the internet. All that is recorded is the connection to the VPN server. As you only have to open one port for the VPN, you reduce the attack surface. Of course, the VPN provider should be selected carefully.
Access via VPN generally has the following advantages:
You can find instructions on how to set up a VPN on a Synology NAS here.
If you implement the safety tips described above, you should be in a relatively good position. However, not everything is said and done. The topic is so complex that it never hurts to keep researching and rethinking/redefining your own security concept.
In addition to this, there are also rules of behaviour that you should set yourself. For example, you should think carefully about whether and to whom you want to entrust logins for certain services. Only give out access data very carefully. In addition, it is always important to use common sense. If you also use your NAS as a mail server, clicks on suspicious links are of course taboo. Especially if they have been forwarded to your local network.
Want one last tip? Well, I have one more: You can activate notifications on most NAS. For example, a notification by email, which is sent as soon as someone makes a successful or incorrect login attempt.
So, that's the end of the story for now. If you have any other important points that have not been mentioned here, I would be very grateful for your tips. I will also be happy to expand/update the article with them if necessary.
I find my muse in everything. When I don’t, I draw inspiration from daydreaming. After all, if you dream, you don’t sleep through life.
Practical solutions for everyday problems with technology, household hacks and much more.
Show all